“A pitfall in cyber defense Transfer of Technology contracts is dependence on vendors. CyberArmour ensures that the procuring government’s/institution’s designated individuals receive comprehensive training to independently operate and modify procured cybersecurity technology.”
With global exposure, CyberArmour has developed significant industry linkages with suppliers and vendors that offer cutting edge cybersecurity solutions for both IT and OT domain areas. Furthermore, we ensure that your team receives specific training to customize and operate these technologies independently while ensuring continued O&M simultaneously.
We understand that procuring a cybersecurity solution is not a simple transaction. Get in touch with us for a discussion on your specific needs. Some of the solutions we offer fall into the following categories:
-
Asymmetric Cryptographic Encryption Solutions for secure network and mobile communications
-
AI-Powered Deception Platforms (Shadow Networks)
-
Security Information and Event Management (SIEM) / Security Orchestration, Automation, and Response (SOAR) Solutions
-
Security Operations Center (SOC) enablement
1. Asymmetric Cryptographic Encryption Solutions for Secure Network and Mobile Communications
The application of asymmetric cryptographic algorithms to convert data into an unreadable format. Encrypted data can only be accessed by authorized users with the corresponding decryption key. This provides a secure way to communicate sensitive information without the risk of interception or unauthorized access. Designed with a military organization’s functions, applications, and security challenges in mind, Asymmetric Cryptographic Encryption Solutions are at the cutting edge of quantum secure cyber defense that act as last line of defense in an on-going cyberattack. Furthermore, these solutions allow for:
- Independent and customer controlled secure network encryption through implementation and use training.
- Remote mobile/portable capabilities.
- Secure infrastructure for email, voice, chat, etc.
- Protection of mission critical networks and functions.
- Multiple layers of security controls for restricted communications.
- Adequate security at all levels.
- Central control through enterprise deployment at customer premises.
The solution incorporates Rack, Desktop, and Personal encryption units, configured by the customers themselves to allow for unparalleled security and unparalleled control over cyber defense.
Leveraging Encryption for Inclusion of Mobile Devices into Secure Network and Enabling Encrypted Mobile Storage.
Central Control through Enterprise Deployment on your Premises.
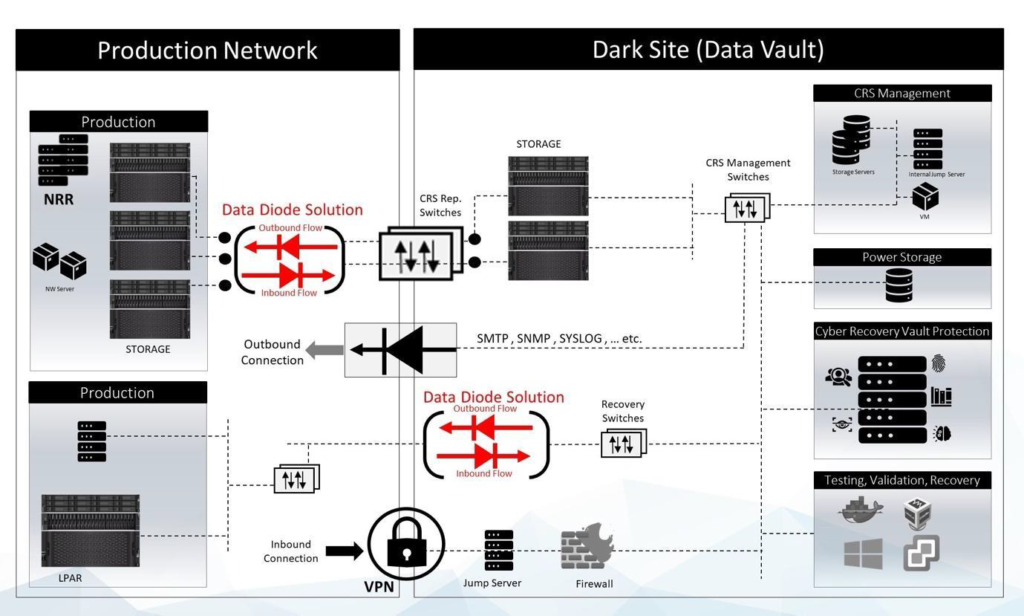
Data Diodes:
Military grade, hardware based, cyber security solution to establish network segmentation between production networks and data vaults as a security measure against cyber risks, while maintaining effective communications between the two: Data Diodes. Network segmentation is one of the most effective methods when mitigating cyber risks. The two primary categories of network segmentation are physical segmentation and logical segmentation. Physical segmentation exhibits an advantage over logical separation when segmenting networks. The latter approach is more susceptible to cyber-attacks as attacks exploit vulnerabilities in the network or device software. Physical separation on the hand is a much more complex system to bypass. Data Diodes are physical segmentation devices that allow data to flow in only one direction as the diode is based on hardware enforced routing and does not use software or firmware.
These characteristics make them effective at preventing data exfiltration from networks. Data diodes allow a secure mechanism to connect the data vault and the production network. They can be configured to allow for two independent data flows to eliminate any risk of compromise, side channel leakage, or lateral movement. This configuration enables two-way communications while keeping the security measure intact. In this particular configuration, the diodes modify the Media Access Control (MAC), Internet Protocol (IP), and Transmission Control Protocol (TCP) port values when transferring data between the production network and the data vault. The address translation ensures that each network is masked relative to the other in terms of number of machines and network architecture. These actions imply that threat actors cannot execute network mapping, a critical first step in the cyber kill chain (the generic steps employed in every cyber-attack).
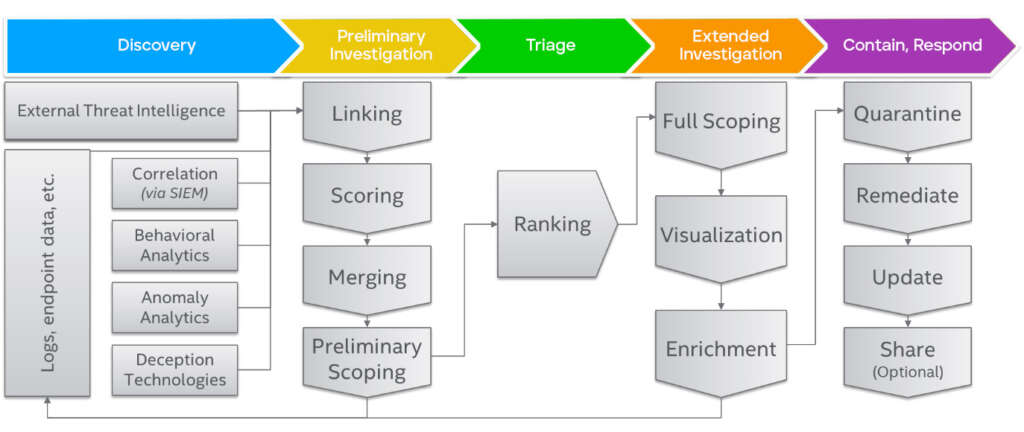
2. AI-Powered Deception Platforms (Shadow Networks)
The next stage in the evolution of honeypots and breadcrumbs-based deception technology. AI powered Deception Platforms replicate normal network conditions using tunneling, network intrusion diversion, virtual machines, and network infrastructure obfuscation technology to deceive and track threat actors.
Derived from the concept of ‘deception’, shadow networks are fake networks that threat actors are led to when secure systems are under attack.
A shadow network is hosted as a ‘deception farm’. Whenever a supported network is invaded by a threat, the system detects and directs the threat actor to a replica of the targeted network. The replicated network behaves exactly as the originally targeted network. Thus, creating the element of deception.
Shadow Networks deliver a two fold advantage. First, information in the original networks stays secure because the threat actor is accessing fabricated information. Second, it allows the farm managers to perform ‘mind hunting’; understanding the objectives of the threat actor and the tools the actor uses in an
attempt to accomplish the mission enabling us to map an APT’s motive.
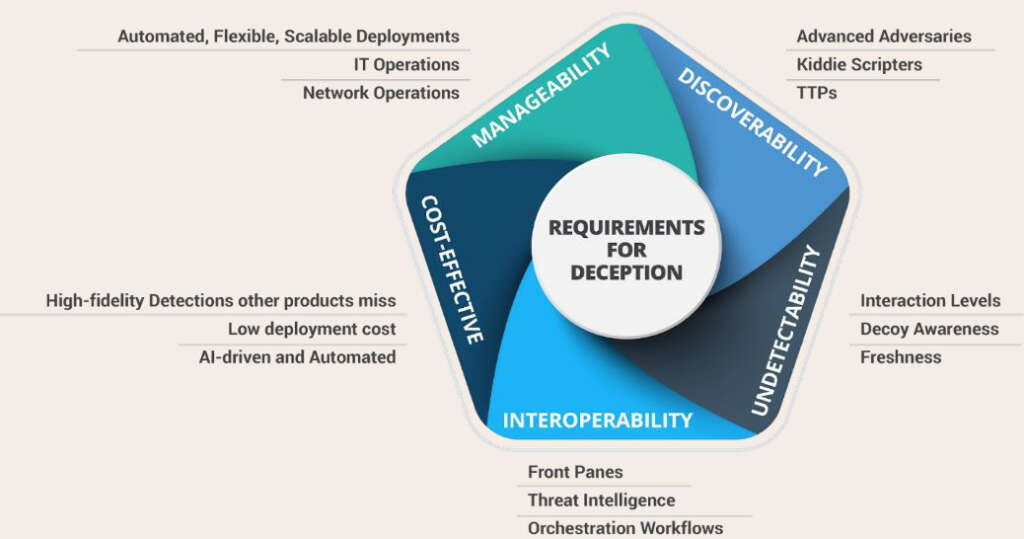
Two strategies can be employed to pursue the development of deception farms. A generic deception farm is a cloud which hosts pre-fabricated instances of networks which are to be protected. Whereas, a ‘Just-in-Time’ deception farm virtually fabricates the network under threat in a cloud environment, in real time through warm standby, in a scalable manner from a resource perspective.
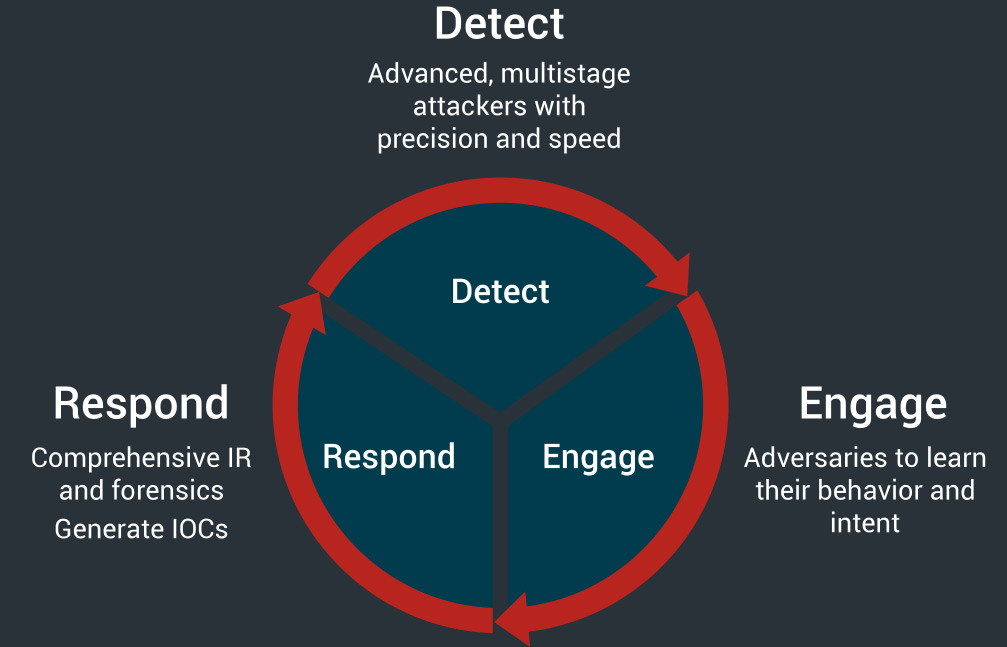
Solution Lifecycle Capabilities
Deception Palette
The most comprehensive palette of deceptions would include: lures, breadcrumbs, bait and decoys. This pervasive approach would allow Government departments to launch an effective and efficient campaign to combat advanced attackers. The proposed project would allow replication of behavior of
assets that are not otherwise easily virtualized or emulated [examples include IoT devices, Routers,Switches, ICS controllers, etc.]
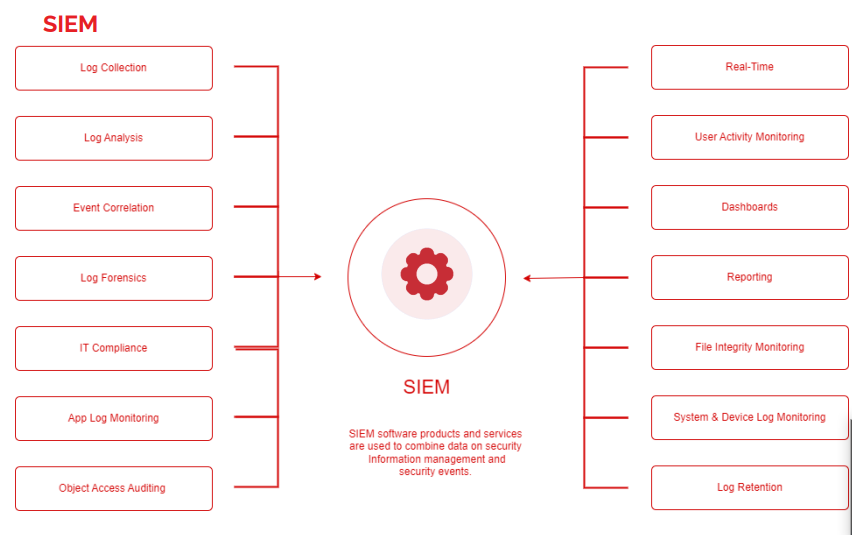
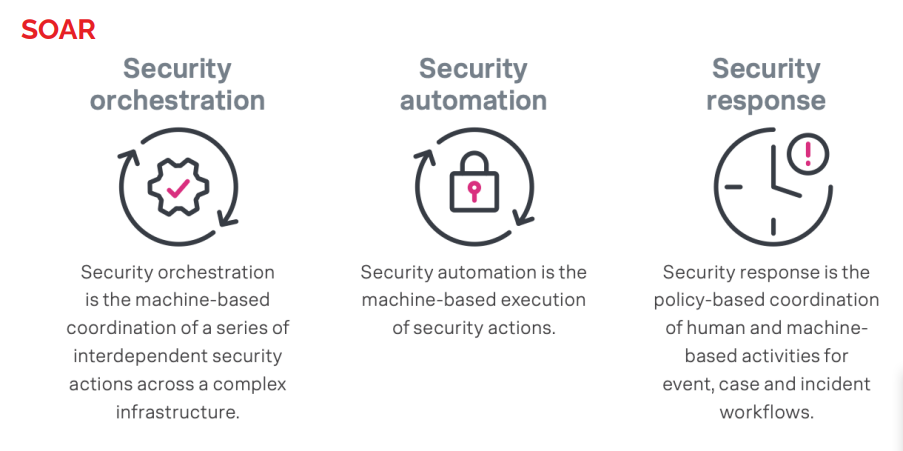
3. Security Information and Event Management (SIEM) /
Security Orchestration, Automation, and Response (SOAR) Solutions
SIEM provides real-time threat detection and alerts, while SOAR automates and streamlines incident response activities. Together, these solutions can help organizations identify and respond to security incidents quickly and effectively, minimizing the impact of cyber threats on their operations.
4. Security Operations Center (SOC) enablement
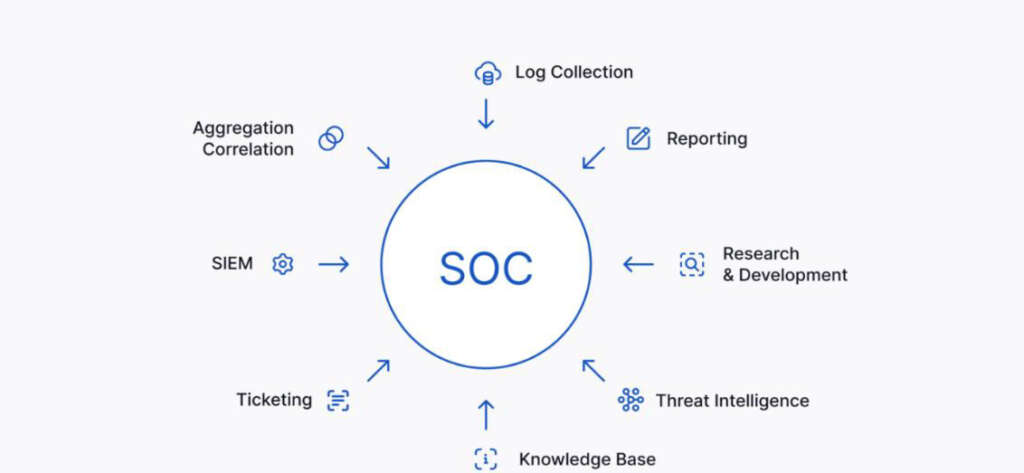
A centralized team/facility responsible for monitoring, detecting, analyzing, and responding to cybersecurity incidents and threats. The SOC is staffed with cybersecurity professionals who use a variety of tools, techniques, and processes to monitor the organization’s network, systems, applications, and data for security events and anomalies.
Overview of SOC Solutions:
Workflow of a SOC Solution: